Financial advisors today must not only be experts in financial strategies but also in the art of...
For enterprise product & platform leaders who need a clear, pragmatic path to launch a secure, reusable internal portal (i.e. a digital document vault or shared client workspace) that multiple business units can consume. This playbook equips enterprise teams to deploy, operate, govern, and scale a secure vault platform built for trust, transparency, and repeatable value.
Why this makes sense now (strategic context):
-
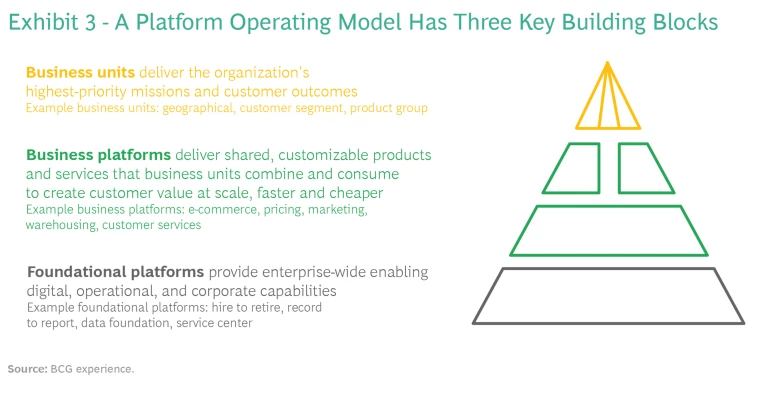
Enterprise reuse at scale. A platform operating model (POM) treats shared capabilities—like a portal for secure document exchange—as products consumed across business lines. It reduces duplication, speeds delivery, and concentrates scarce talent in high-leverage teams.
-
Reliability and transparency by design. Publishing Service Level Objectives (SLOs) with error budgets lets you make data-driven trade-offs between new features and stability—exactly how modern platform teams maintain trust with internal customers.
-
Security as table stakes. A portal that moves PII and regulated content should adopt Zero Trust (no implicit trust; continuous verification) as its default stance. Use the NIST reference model to anchor architecture and control discussions.
The Business Context - Platform Operating Models
In today’s fast-moving wealth and financial services landscape, efficiency and consistency aren’t optional—they’re table stakes. At SideDrawer, our digital vault doesn’t just house documents—it powers a platform operating model (POM) that transforms how large firms deliver secure document exchange at scale.
What the Platform Operating Model Means for You
-
Enterprise‑Grade Reuse: Rather than reinventing secure vault access or workflows for every business unit, SideDrawer offers a shared, API-driven platform. This reduces redundancy, accelerates launches, and lets your high-leverage teams focus on innovation—not plumbing.
-
Strategic Governance, Continuous Delivery: Our platform approach enables centralized governance—meaning you can roll out shared features like advisor-client integrations, automated onboarding, or batch document shipments across lines of business with speed and consistency.
What This Means for Your Organization
-
Faster Time‑to‑Value: Business units can build on top of the vault using our “golden path”—sandbox environments, widgets, APIs, and reference implementations—all supported out of the box to ensure integrations happen in days instead of months.
-
Unified Reliability: Platform-level design means SLOs, dashboards, incident response, and operational standards are standardized across initiatives resulting in predictable performance and smoother governance reviews.
-
Built for Zero Trust: Security isn’t an afterthought, it’s baked in. SideDrawer’s zero‑trust posture (inspired by NIST) ensures continuous authentication, audit-ready access, and vendor‑ready architecture with no one-offs, no exceptions.
At a Glance: Platform Element Highlights
| Platform Element | What It Delivers for Your Firm |
|---|---|
| Golden Path Toolkit | Sandboxes, Postman collections, widgets—integrate rapidly and consistently across business units. |
| Shared SLO/Error‑Budget Framework | Uniform reliability and stability, paired with centralized monitoring and transparency. |
| Governance & Enablement Tools | Platform Council frameworks, scorecards (e.g. impact/effort), cycle‑time metrics for better decision making. |
| Exit & Portability Playbook | Ensures migration readiness, portability, and vendor-agnostic flexibility from day one. |
Service Level Objectives - Creating Accountability
At SideDrawer, we know that trust is earned through performance you can measure. That’s why we apply the same discipline used by leading enterprise platforms: Service Level Objectives (SLOs) and error budgets.
In simple terms:
-
SLOs define the quality of service you should expect from us.
-
Error budgets provide transparency into the small amount of downtime or delay that can occur, while ensuring issues are always addressed quickly.
Real SLOs To Apply
This model gives you confidence that your vault is not only secure, but also consistently available and responsive for your teams and clients. Your enterprise implementation of the vault will likely involve a system configuration that meets with the IT data residency and premise management needs. This means that you will need to have clarity around performance and who is responsible for what aspects of that performance, including clear security considerations.
These are examples of real SLOs across the areas that matter most to advisors, enterprises, and regulators:
-
Availability – The vault is accessible 99.9% of the time (less than 45 minutes downtime per month).
-
Speed – 95% of file uploads under 50MB complete in 3 seconds or less.
-
API Performance – 99% of requests return results in under 1 second, supporting seamless integration with CRMs, wealth platforms, and other systems.
-
Security & Compliance – All authentication and authorization flows require MFA and role-based access. Unlike other SLOs, security is held to a zero-tolerance standard.
-
Data Durability – Your documents are backed by cloud-grade durability guarantees (11 nines, or 99.999999999%), verified through restore tests.
Understanding Error Budgets
Every SLO comes with an “error budget” — the acceptable margin for small, non-critical service issues. For example: With a 99.9% availability SLO, we allow for up to 43 minutes of downtime per month. If that budget is consumed, every subsequent outage becomes unacceptable until the root causes have been corrected. This approach holds everyone accountable, while giving you visibility into service quality in a way that connects directly to business impact.
Zero Trust Architecture (and What “Good” Looks Like)
Zero Trust isn’t just a security feature, it’s a design philosophy. At SideDrawer, we build our vault platform so that every interaction, every access, and every data flow is authenticated, authorized, and observable. This means your firm doesn’t just get a secure application, you get a vault designed from the ground up for regulatory trust and enterprise resilience.
Core Principles of Zero Trust, Brought to Life in Architecture
| Zero Trust Principle | What It Means in Practice | How SideDrawer Delivers It |
|---|---|---|
| Verify Everything, Always | No user, system, or request is trusted by default. | SSO with MFA across all access paths, granular RBAC, scoped API tokens. |
| Least-Privilege Access | Users and integrations see only what they need, nothing more. | Policy-driven authorization, role-based access, client/workflow segmentation. |
| Immutable Audit Trail | Every action is logged and provable. | Tamper-proof logs, event-driven architecture, centralized log pipelines, regulator-ready exports. |
| Secure Data Plane | All data remains confidential and integrity-protected. | AES-256 encryption at rest, TLS 1.3 in transit, data residency and retention enforced as policy. |
| Observability Everywhere | Trust is continuously monitored and measured. | Built-in metrics, distributed tracing, SLO dashboards visible to business and IT stakeholders. |
In today’s financial services world, threats come from all directions—not just outside the firewall, but also from compromised devices, email phishing, and insider risks. At SideDrawer, we don’t assume trust—we verify and enforce it continuously. That’s the Zero Trust model in action.
What Zero Trust Means for You
-
Verify Everything, Always - Every access request, whether it comes from a user, advisor, or integration, must authenticate via SSO, enforce MFA, and respect strict role-based permissions, every single time. No more implicit trust based on network location.
-
Least-Privilege Access - Users and systems are only granted the access they absolutely need. For instance, an external accountant sees only the folder with the documents they’re collaborating on, nothing more, nothing less.
-
Immutable Audit Trail - Every action (file uploads, downloads, shares, or permissions changes) is logged in a tamper-proof audit record. This ensures compliance with SOC-2, PIPEDA, GDPR, and other regulatory requirements.
-
Secure by Design - SideDrawer’s architecture replaces email-based document exchange with an authenticated vault environment, removing attachments from inboxes and neutralizing phishing vectors.
Why This Matters for Your Enterprise
-
Unified Trust Model: Security isn’t bolted on — it’s woven into the vault’s operating model, across identity, data, and observability.
-
Compliance Readiness: Every architectural control aligns to standards like NIST SP 800-207, SOC 2, and GDPR, making audits faster and less disruptive.
-
Operational Transparency: Dashboards don’t just measure uptime — they show whether trust principles are being enforced in real time.
-
Client Reassurance: You can tell your clients, “Every single action is authenticated, authorized, and logged.” That’s trust you can demonstrate.
Where to Start
Standing up an enterprise vault doesn’t have to be overwhelming. The key is to begin in a way that matches your organization’s context, risk posture, and readiness. SideDrawer’s playbook is designed to be modular—so you can start small, prove value, and scale quickly across business units.
Three Common Starting Paths
-
Pilot-Focused - Select a single line-of-business (LOB) or workflow (e.g., tax season document collection, KYC onboarding, or advisor–client document exchange). This lets you validate the vault in a contained environment, gather user feedback, and demonstrate measurable results before expanding.
-
Governance-First - Form a small Platform Council with representatives from IT, Compliance, Security, and a line of business. Use this group to define the vault’s mission, access boundaries, and intake criteria, ensuring enterprise alignment from day one.
-
Compliance-Driven - Anchor the rollout around regulatory priorities such as audit logging, SOC-2 reporting, or document retention requirements. This ensures early credibility with risk and compliance teams, and accelerates adoption in regulated areas.
Who Should Be Involved
-
Platform Lead: Defines the pilot scope and vault boundaries.
-
Security/Compliance: Reviews and enforces Zero Trust policies, ensures audit readiness.
-
IT/Ops: Implements SLO dashboards, monitors error budgets, and manages integrations.
-
Business Unit Lead: Champions adoption, collects feedback, and shares success metrics.
A Practical Roadmap
-
Write the mission & boundaries (1 page). What the system provides (APIs, widgets, events, audit) and what it doesn’t (LOB-specific workflows). Tie to POM goals: agility, resilience, talent leverage.
-
Pick 2–3 high-impact journeys. E.g., onboarding document collection, advisor–client document exchange, collateral packages. Make sure to have a bias towards use cases that have cross-LOB reuse.
-
Stand up the “golden path.” Ship a sandbox, reference app, Postman collection, and an upload/share widget so consuming teams integrate in days, not months. (Mirror GOV.UK’s service-team clarity on roles/skills as you staff.)
-
Publish initial SLOs + error budgets (availability, p95 latency, webhook success) and align incident comms. Then iterate using Google SRE’s step-by-step recipe.
-
Pilot with one business line; measure cycle time, first-time-right, adoption, support load. Use findings to harden the golden path.
How to Triage Business Intake - Focus on Impact First
When requests for vault enhancements or new workflows come in, it’s critical to triage them systematically. Our intake model balances business value, compliance drivers, and technical feasibility to ensure the vault delivers the right outcomes quickly.
Step 1: Score Each Request
We use a weighted 1–5 scoring model:
-
Business Value (30%) – revenue impact, client experience lift, or risk reduction.
-
Feasibility (20%) – ease of integration, data readiness, and access control fit.
-
Urgency & Compliance (15%) – regulatory deadlines, audit findings, or legal requirements.
-
User Experience Lift (15%) – measurable friction eliminated for staff or clients.
-
Reuse Potential (10%) – ability to extend across multiple lines of business.
-
Time-to-Value (10%) – can we deliver it within 90–120 days?
Step 2: Visualize with Impact × Effort
Plot the short list on a simple 2×2 matrix with a focus on Quick-Wins (high impact, low effort → implement first) and then Strategic Bets (high impact, high effort → plan next):

Step 3: Share and Act
Review the intake matrix quarterly in your Platform Council, and share decisions with stakeholders. This ensures transparency, builds trust, and keeps everyone aligned on where the vault is delivering the most impact.
Platform Model Governance (Run It Like a Product)
To scale an enterprise vault effectively, governance must be as methodical as it is strategic. Here’s how SideDrawer’s product-oriented governance model ensures alignment, reliability, and resilience:
At-a-Glance Governance Cadence
| Forum | Cadence | Purpose | Who's Involved |
|---|---|---|---|
| ABR / QBR (Executive) | Quarterly | Set strategy, approve funding, decide central vs local control | CTO, CPO, Risk/Compliance leads |
| Platform Council | Monthly | Triage new requests, surface dependencies, schedule releases | Platform PM, LOB Product Owners, Integration Owners |
| Design Authority | Bi-weekly | Approve architectural patterns, policy-as-code, versioning standards | Security Architect, Compliance Lead, Enterprise Architect |
| Reliability Review | Weekly | Monitor SLOs, error budgets, incidents, and operational backlog | SRE Lead, Platform Ops |
Artifacts That Keep Governance Tangible
-
Service Catalog & Consumer Checklist: Consumer-facing vault capabilities (APIs, events, widgets, SLAs), ensuring teams can self-serve.
-
Policy-as-Code Libraries: Codified consent, retention, and data residency controls, with pre-prod gating.
-
Versioning & Deprecation Policy: Clear 12–18 month supporter timelines, enabling stable ecosystem growth.
-
Exit & Portability Runbook: Ready-made export and audit flows to ease third-party diligence.
Funding & Incentive Models
Governance isn’t complete without aligning incentives to consumption. To prevent unlimited intake requests and ensure sustainable growth, SideDrawer recommends implementing an internal showback/chargeback model:
-
Showback – Report usage (storage, API calls, onboarding workflows) by business unit, without direct billing. Builds awareness and transparency.
-
Chargeback – Allocate costs proportionally to usage, encouraging responsible demand management and ensuring teams prioritize high-impact requests.
These models are reviewed in ABRs/QBRs and Platform Councils, ensuring leaders see how vault resources are being consumed, where demand is growing, and when new investment is justified. By treating the vault like a product with a transparent economic model, enterprises avoid the “free, unlimited” trap, align consumption with strategic priorities, and create a sustainable platform roadmap.
The Feedback Loop in Motion
-
Reliability Reviews identify risks and operational insights.
-
Platform Councils use intake data, usage metrics, and cost transparency to prioritize initiatives.
-
ABRs/QBRs use these insights to set strategy, allocate funding, and recalibrate the platform roadmap.
This cycle closes the loop between technical performance, governance forums, and financial accountability—ensuring the vault evolves as a resilient, enterprise-grade product.
Common FAQs (and Crisp answers)
Q: Why should we centralize this portal instead of letting each BU build its own?
A: Platform Operating Models outperform matrixed “every team builds everything” approaches on speed, resilience, and talent leverage by standardizing shared capabilities and reducing duplication. Reuse is the ROI.Q: What SLOs should we start with?
A: Publish availability, p95 API latency, and webhook-delivery SLOs. Use error budgets to govern release pace vs. reliability work (with alerting tied to budget burn). (sre.google)Q: How do we keep security strong without killing usability?
A: Implement NIST Zero Trust principles (continuous authentication/authorization; least privilege) behind simple UX primitives (SSO, short-lived tokens), and codify policy in pre-prod tests. (NIST Publications)Q: What’s a fair way to bill Business Units?
A: Begin with showback (visibility) and shift to chargeback once the cost-allocation model is accurate. Use TBM for activity/consumption modeling and FinOps for the operating playbook. (TBM Council, finops.org)Q: How do we prevent “side doors” and one-off integrations?
A: Enforce the golden path: API gateway registration, event schema review, SLO sign-off, and certification before prod. Socialize via the Platform Council and enablement sessions. (GOV.UK)Q: What governance meetings are must-have vs. nice-to-have?
A: Must-have: ABR/QBR (strategy & funding), Platform Council (demand & sequencing), Design Authority (standards & versioning), Reliability Review (SLOs & incidents). (BCG)Q: We don’t have all the people—who are the minimal roles?
A: Platform PM/TPM, core platform engineers (APIs/widgets/events), an SRE (shared), and part-time Security/IAM + Records/Privacy. Use GOV.UK’s role guides to shape job descriptions. (GOV.UK)
Enterprise Vault Playbook: From Plan to Platform
You’ve now laid the architectural, operational, and governance foundation of a secure, reusable vault platform. What comes next?
| Pillar | What You’ve Achieved | What’s Next |
|---|---|---|
| Define & Prototype | Mission, boundaries, service catalog, golden path tooling | Stand up a user-visible feedback loop and refine your MVP with pilot teams |
| Operate & Measure | Initial SLOs, dashboards, and status page in place | Set up reliability reviews and expand dashboards to business owners |
| Govern & Secure | Governance bodies formed, Zero Trust architecture codified, intake scoring live | Hold governance reviews, calibrate policies, and ensure security maturity |
| Govern Financial Levers | Showback designed, chargeback readiness assessed, exit runbook reviewed | Pilot financial models, align with FinOps/TBM practices |
Next Steps for Sustained Momentum
-
Anchor Reliability Governance — Host reliability reviews and capture insights as inputs into the Platform Council roadmap.
-
Extend Golden Path Awareness — Enable more lines of business with workshops, integration clinics, or sandbox onboarding.
-
Pilot Financial Models — Start with internal visibility (showback), then transition to chargeback where adoption and cost visibility is mature.
-
Measure Trust — Create a “Vault Trust Report” for internal or client consumption—highlight uptime, adoption, audit readiness, and cost efficiency.
Closing Thought
SideDrawer’s vault is not just a storage system—it’s a product-caliber, enterprise-grade platform engineered for trust: resilient, transparent, auditable, and cost-aligned. As your team moves from playbook to practice, each metric, policy, and governance decision will reinforce the credibility and value of your vault deployment.
If you want to learn more about Digital Vaults, User Adoption Approaches or any other topics, please feel free to review the other SideDrawer blog posts.






.png)